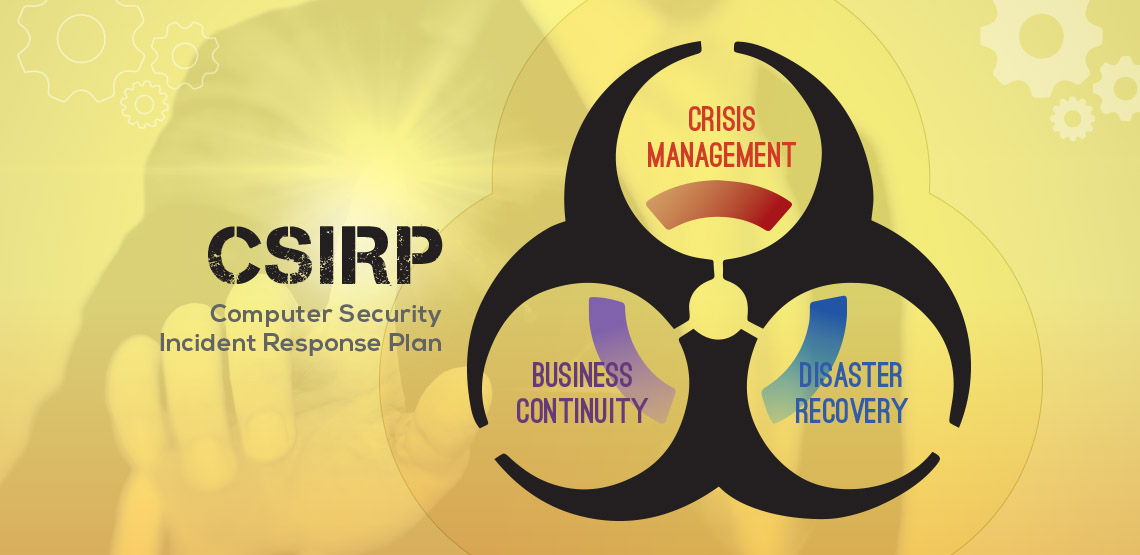
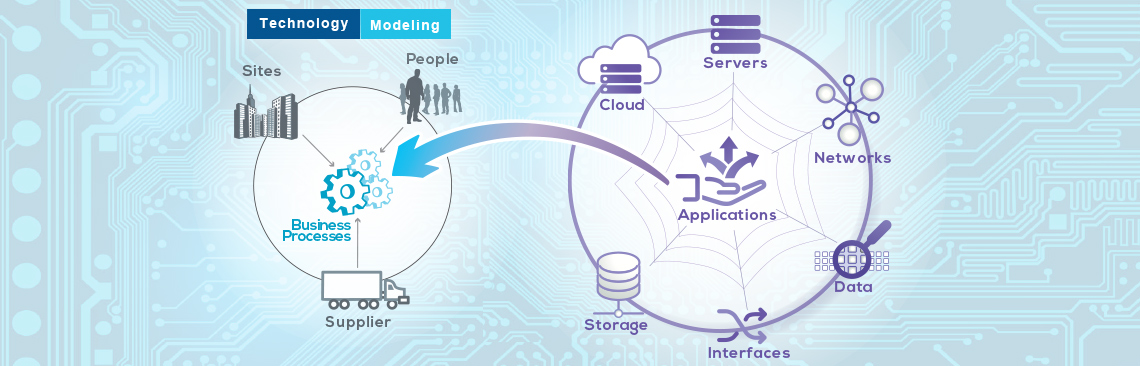
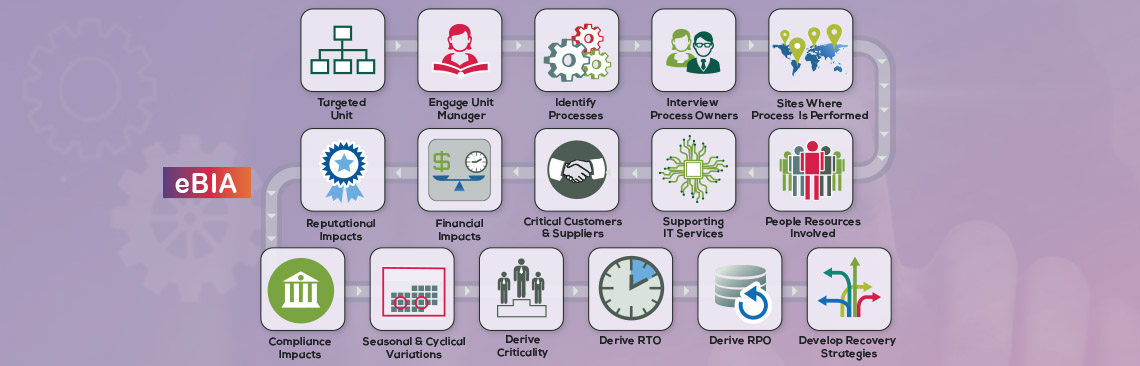
Agencies of the US Federal Government (but Canadian, EU and most other Government agencies as well) have a ‘civic duty’ to provide Continuity of Operations (COOP) to assure the delivery of services to their citizens (as well as other Government operations).
In many ways this mandate is no different than the goals or objectives of Business Continuity Management in the private sector. But there are some differences. Those unique needs require unique solutions. This is clearly a case of one size not fitting all.
Information Security
If there are lessons to be learned from recent data breaches within the US Government, perhaps the most obvious is that information security is of paramount importance. In the private sector, BCM information security is increasingly of concern. Within Government Agencies, where SAML2 and ADS authentication have long been common, two-factor authentication (smart cards or biometrics in addition to user names and passwords) are rapidly becoming the norm. This creates some limitations for many Agencies; only BCM software which can accommodate PKI/CAC authentication is acceptable – and most don’t. Even with those efforts, while much of the business world seems to be moving toward cloud-hosting, government generally opts for the self-hosted camp.
Simultaneously, for the majority of federal agencies, data encryption (for both data in-transit and data at rest) has become mandatory. Both of these security requirements subject web-based BCM tools to considerable scrutiny by Agency Information Security teams as part of the RFP and due diligence process.
Adding another layer of complexity are requirements within the US Federal Information Security Management Act (FISMA) guidelines. Most Agencies also need to acquire Department of Defense (DOD) DIACAP certification (DIACAP are the DOD requirements for risk management of information systems)
Compliance
How US Federal Agencies create, maintain and test their BCM plans must comply with both the Federal Preparedness Circular 65 (FPC65) and Dept. of Homeland Security (DHS) guidelines. At the same time, most of those US Federal Agencies must also accommodate the National Incident Management System (NIMS) guidelines. And as mentioned earlier, Agency DR planning must meet FISMA guidelines (while continuing to comply with DIACAP).
One unique aspect of US Government Agency use of IT applications (including BCM) is the requirement to comply with VPAT-508 (Voluntary Product Availability Template, under Section 508 of the Rehabilitation Act) to assure that all employees have equal access to software products, regardless of visual or physical impairment.
Not only are Federal Agencies subject to such internal regulations (and auditing), they are also vulnerable – whenever any perceived ‘failure’ occurs – to both Executive and Legislative Branch scrutiny. While private enterprises need not divulge security failures or disruptions that don’t directly impact their customers, government agencies have no such luxury: with media attention, their problems only escalate when an attempt is made to sweep information security breaces under the proverbial rug.
Incident Management
NIMS guidelines govern the Incident Management requirements for all Federal Agencies (as well as many other government institutions, regulated enterprises and private businesses). BCM plans for Agencies must be built with NIMS Incident Management guidelines in mind, and integrate well with the use of the Incident Command Systems (ICS), including utilization of required ICS forms for management and reporting.
Risk and Threat Management
And while there are parallels in private enterprise, some Federal Agencies are frequent targets – of hackers, fraudsters, and foreign intelligence efforts – not to mention threats from ‘disgruntled citizens’, which are much more numerous than those occasionally making news headlines.
Conducting an annual Risk Assessment is not enough; simply tracking threats is not enough. Agencies must maintain constant vigilance and be prepared to take action to prevent threating activities from escalating, and be prepared to react to those that cannot be anticipated. Government agencies aren’t protecting profits – they’re protecting citizens. That’s the difference.
Click here if you are a Federal Agency looking for a solution.