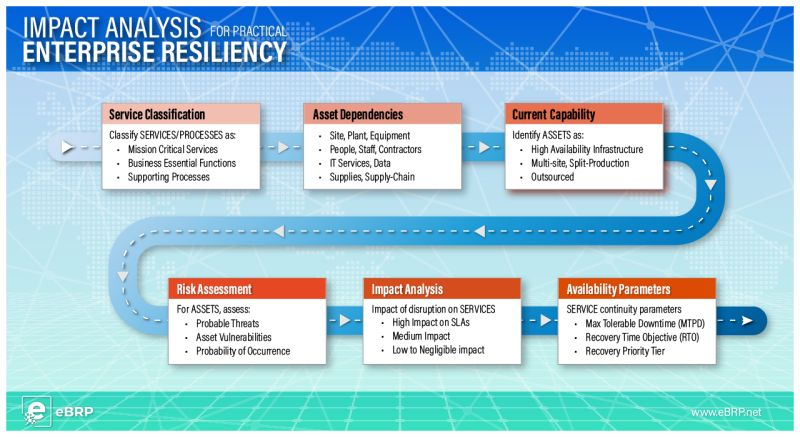
Ensuring enterprise resilience involves evaluating service criticality, analyzing asset dependencies, and assessing current capabilities while addressing risks and potential disruptions. This process identifies vulnerabilities, threats, and availability parameters to safeguard the organization’s mission, reputation, and service levels.
𝗦𝗲𝗿𝘃𝗶𝗰𝗲 𝗖𝗹𝗮𝘀𝘀𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻 helps determine the importance of services by tiering them into 𝘮𝘪𝘴𝘴𝘪𝘰𝘯-𝘤𝘳𝘪𝘵𝘪𝘤𝘢𝘭, 𝘣𝘶𝘴𝘪𝘯𝘦𝘴𝘴-𝘦𝘴𝘴𝘦𝘯𝘵𝘪𝘢𝘭, and 𝘴𝘶𝘱𝘱𝘰𝘳𝘵𝘪𝘯𝘨 𝘧𝘶𝘯𝘤𝘵𝘪𝘰𝘯𝘴. Oversight from senior executives ensures proper alignment with organizational goals.
𝗔𝘀𝘀𝗲𝘁 𝗗𝗲𝗽𝗲𝗻𝗱𝗲𝗻𝗰𝗶𝗲𝘀 must be mapped to services using authoritative sources such as HRM, IT CMDB, and VMS. This analysis reveals how disruptions to sites, personnel, technology, or supplies may compromise service levels, often showing that 80% of assets support 20% of the critical functions.
𝗖𝘂𝗿𝗿𝗲𝗻𝘁 𝗖𝗮𝗽𝗮𝗯𝗶𝗹𝗶𝘁𝘆 assessment identify operational 𝘨𝘢𝘱𝘴 and 𝘴𝘪𝘯𝘨𝘭𝘦 𝘱𝘰𝘪𝘯𝘵𝘴 𝘰𝘧 𝘧𝘢𝘪𝘭𝘶𝘳𝘦 in infrastructure, 𝘮𝘶𝘭𝘵𝘪-𝘴𝘪𝘵𝘦 𝘱𝘳𝘰𝘥𝘶𝘤𝘵𝘪𝘰𝘯, and 𝘰𝘶𝘵𝘴𝘰𝘶𝘳𝘤𝘦𝘥 𝘴𝘦𝘳𝘷𝘪𝘤𝘦𝘴. Evaluating high-availability setups and supplier resilience is crucial to understanding existing operational strengths and weaknesses.
𝗥𝗶𝘀𝗸 𝗔𝘀𝘀𝗲𝘀𝘀𝗺𝗲𝗻𝘁𝘀 leverage asset mapping and capability evaluations to highlight areas requiring stronger controls. Threat likelihood is assessed through historical data and situational analysis, identifying where vulnerabilities could impact operations.
𝗜𝗺𝗽𝗮𝗰𝘁 𝗔𝗻𝗮𝗹𝘆𝘀𝗶𝘀 determines the effects of disruptions on services. Mission-critical services are often highly affected, while essential functions and supporting processes experience moderate to low impacts.
Using this analysis, 𝗔𝘃𝗮𝗶𝗹𝗮𝗯𝗶𝗹𝗶𝘁𝘆 𝗣𝗮𝗿𝗮𝗺𝗲𝘁𝗲𝗿𝘀 such as Maximum Tolerable Period of Downtime (𝗠𝗧𝗣𝗗), Recovery Time Objective (𝗥𝗧𝗢), and 𝗥𝗲𝗰𝗼𝘃𝗲𝗿𝘆 𝗧𝗶𝗲𝗿 are established to guide continuity strategies.
A thorough evaluation of dependencies, risks, and impacts enables prioritization of critical operations. By addressing vulnerabilities and defining clear recovery objectives, organizations can maintain service quality and operational stability during disruptions.